Research Summary
The report discusses the recent frontend attacks on DeFi protocols, including Trader Joe and Velodrome, and how these attacks have led to significant losses. It highlights the Safary hack and the need for users to inspect DeFi transactions before approving them with their hardware wallets to avoid such losses.
Key Takeaways
Understanding Frontend Attacks
- Definition of Frontend Attacks: The report explains that a frontend attack occurs when the website used by a protocol is replaced with malicious code. This allows the attacker to submit an instruction to transfer the user’s wallet balance to an address they control, appearing as a normal Metamask prompt when the user interacts with the website.
- Impact of Frontend Attacks: The report emphasizes that unless users know how to read transactions and are diligent, they could easily approve a transaction that steals all their funds. It cites the example of Nexus Mutual founder Hugh Karp, who lost millions to this simple hack.
Preventing Frontend Attacks
- Importance of Transaction Inspection: The report underscores the importance of inspecting DeFi transactions before approving them with a hardware wallet. This is a crucial step in preventing frontend attacks and avoiding significant losses.
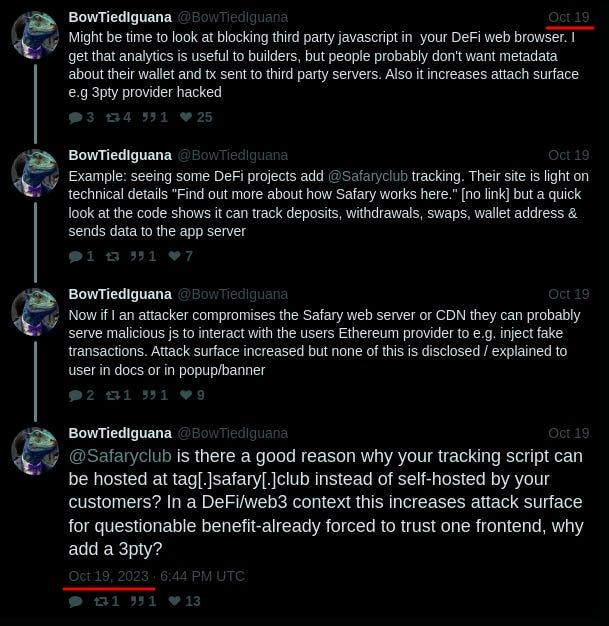
- Case Study – Safary Hack: The report highlights the Safary hack, where the security expert had warned about the attack in general and alerted his suspicions about Safary a few weeks before funds were drained. This case study serves as a reminder of the importance of heeding expert warnings and staying vigilant about potential threats.
Actionable Insights
- Enhance Transaction Security: Users should learn how to read and inspect DeFi transactions before approving them with their hardware wallets. This can help them spot any irregularities and prevent potential frontend attacks.
- Stay Informed About Potential Threats: Users should stay updated about potential threats and heed expert warnings. This can help them avoid falling victim to hacks like the Safary attack.
- Adopt Best Practices for Storing Crypto: Users should adopt best practices for storing crypto to enhance their security. This includes using hardware wallets and following expert advice on crypto storage.